Converting Automotive Standard ASAM ODS XML to a database (PostgreSQL)
In this blog post we will show you how to obfuscate ASAM ODS XML data and convert it to PostgreSQL. For this quick process which will just take a couple of minutes, we will use Sonra’s obfuscation tool Paranoid (open source) and Sonra’s data warehouse automation tool for XML, JSON, and industry data standards Flexter.
The enterprise edition can be installed in the cloud or on-premise.
ASAM
ASAM (Association for Standardization of Automation and Measuring Systems) is a non-profit organization that promotes standardization for tool chains in automotive development and testing.
ASAM members are international car manufacturers, suppliers, tool vendors, engineering service providers and research institutes from the automotive industry. ASAM standards are developed in work groups, composed of experts from our member companies.
For this blog post we will look at the ODS (Open Data Services) standard. This standard has been developed for test data post-processing and evaluation.
Obfuscating ASAM ODS XML
To prevent sharing confidential data, we will start by obfuscating our XML data with Paranoid. To mask data we have to provide a path to our file and a path to an output location. Paranoid will create the folder automatically, no need to create it first.
Optionally Paranoid has the feature to mask individual elements inside of a document.
|
1 |
paranoid -i <file path> -o <output file path> |
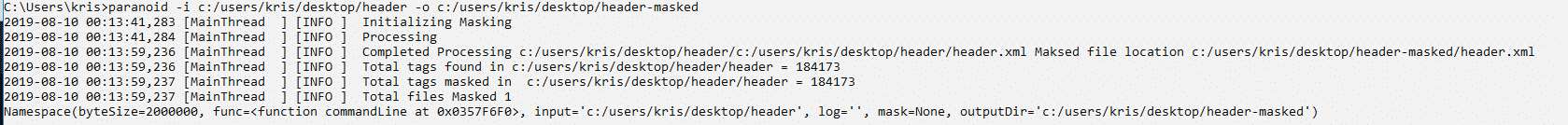
Let’s check the file after obfuscation.
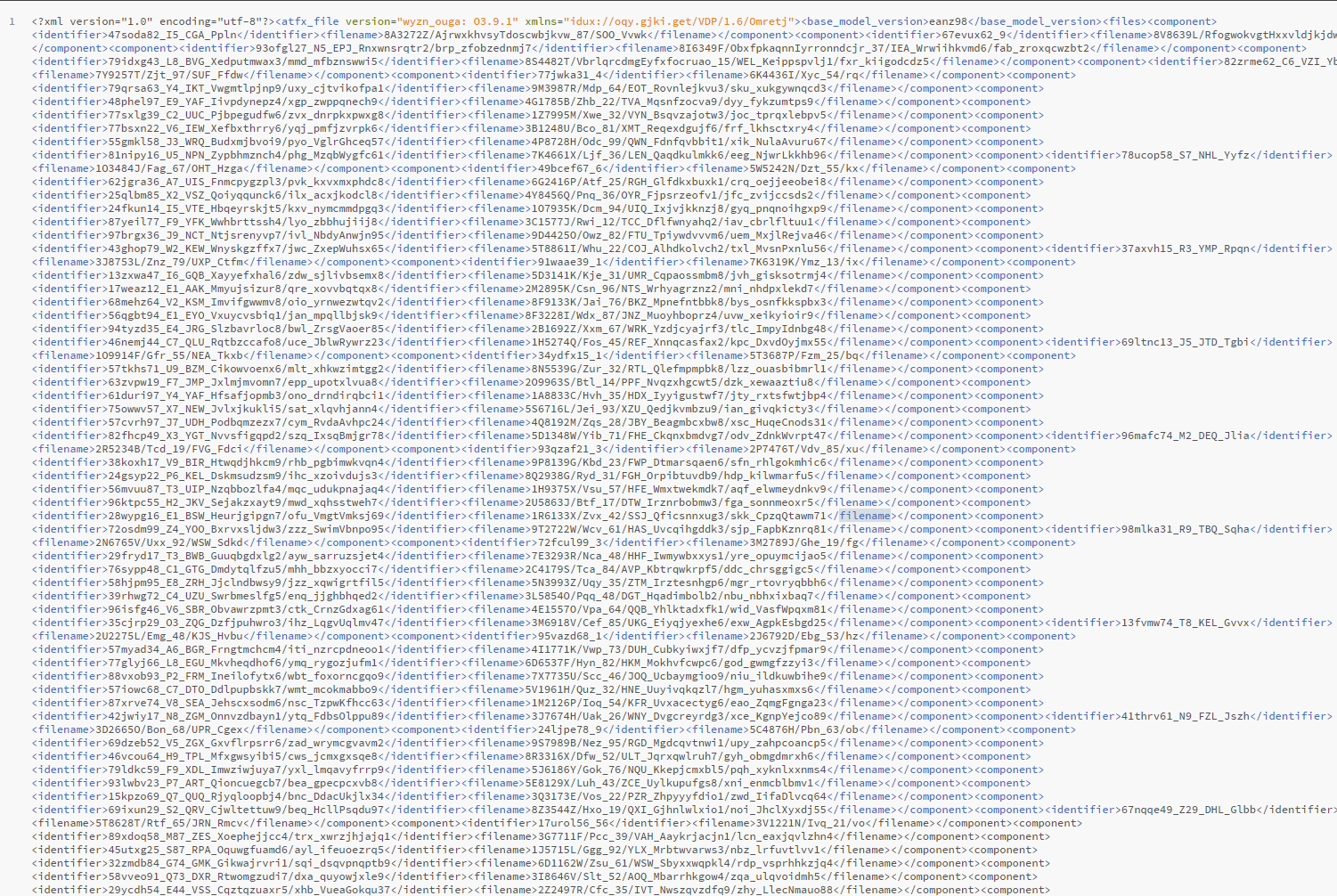
Now we can start with converting our obfuscated ASAM ODS XML data to PostgreSQL.
Processing masked XML with Flexter
Flexter exposes its functionality through a RESTful API. Converting XML/JSON to PostgreSQL can be done in a few simple steps.
Step 1 – Authenticate
Step 2 – Define Source Connection (Upload or S3) for Source Data (JSON/XML)
Step 3 – Optionally define Source Connection (Upload or S3) for Source Schema (XSD)
Step 4 – Define your Target Connection, e.g. Snowflake, Redshift, SQL Server, Oracle etc.
Step 5 – Convert your XML/JSON from Source to Target Connection
Step 1 – Authenticate
To get an access_token you need to make a call to /oauth/token with Authorization header and 3 form parameters:
- username=YOUR_EMAIL
- password=YOUR_PASSWORD
- grant_type=password
You will get your username and password from Sonra when you sign up for the service.
|
1 2 3 4 |
curl --location --request POST "https://api.sonra.io/oauth/token" \ --header "Content-Type: application/x-www-form-urlencoded" \ --header "Authorization: Basic NmdORDZ0MnRwMldmazVzSk5BWWZxdVdRZXRhdWtoYWI6ZzlROFdRYm5Ic3BWUVdCYzVtZ1ZHQ0JYWjhRS1c1dUg=" \ --data "username=XXXXXXXXX&password=XXXXXXXXX&grant_type=password" |
Example of output
|
1 2 3 4 5 6 7 8 |
{ "access_token": "eyJhbG........", "token_type": "bearer", "refresh_token": "..........", "expires_in": 43199, "scope": "read write", "jti": "9f75f5ad-ba38-4baf-843a-849918427954" } |
Step 2 – Define Source Connection (Upload) for Source Data (ASAM ODS XML)
In a second step we upload the ASAM ODS XML source data
|
1 2 3 4 5 |
curl --location --request POST "https://api.sonra.io/data_sources/asamods" \ --header "Authorization: Bearer <access_token>" \ --form "source_type=uploaded_file" \ --form "file=@<file_path>" \ --form "data_type=xml" |
Example of output
|
1 2 3 4 5 6 7 8 |
{ "name" : "asamods", "type" : "xml", "source_type" : "uploaded_file", "path" : "file-06e2f2b9-84cb-4332-ae60-e10f99bf8ffd", "size" : 37500, "create_date" : "2019-08-07T13:41:02.423+0000" } |
Step 4 – Define Target Connection (PostgreSQL)
Since we don’t have a Source Schema we skip the optional step of defining a Source Schema.
We define our Target connection. We give the Target Connection a name and supply various connection parameters to the PostgreSQL database.
|
1 2 3 4 5 6 7 8 |
curl --location --request POST "https://api.sonra.io/target_connections/PostgreSQL-asamods" \ --header "Authorization: Bearer <access_token>" \ --form "target_type=postgresql" \ --form "host=<example.com>" \ --form "username=<pg_user>" \ --form "password=<pg_pass>" \ --form "database=<test_db>" \ --form "schema=<public>" |
Example of output
|
1 2 3 4 5 6 |
{ "name" : "PostgreSQL-asamods", "target_type" : "postgresql", "path" : "xxxxxxxxxxxxxxxxxxxxxxxxxx1.rds.amazonaws.com", "create_date" : "2019-08-14T13:34:10.769+0000" } |
Step 5 – Convert XML data from Source Connection (Upload) to Target Connection (PostgreSQL)
In last step we convert ASAM ODS XML. Data will be written to PostgreSQL Target Connection.
|
1 2 3 4 |
curl --location --request POST "https://api.sonra.io/conversions/asamods" \ --header "Authorization: Bearer <access_token>" \ --form "data_source=asamods" \ --form "target=PostgreSQL-asamods" |
Example of output
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
{ "name" : "DataFlow-1011e136-3168-4879-93a6-1754658d6de6", "schema_source_connection" : null, "data_source_connection" : { "name" : "asamods", "type" : "xml", "source_type" : "uploaded_file", "path" : "file-fa622ed6-6c93-4bd7-9901-b5d122187da3", "size" : 5215515, "create_date" : "2019-08-14T13:47:50.480+0000" }, "target_connection" : { "name" : "PostgreSQL-asamods", "target_type" : "PostgreSQL-asamods", "path" : "xxxxxxxxxxxxxxxxxxxxxxxxxx1.rds.amazonaws.com", "create_date" : "2019-08-14T13:34:10.769+0000" }, "create_date" : "2019-08-14T13:48:04.705+0000", "status" : "I", "download_link" : null, "full_status" : "INITIALIZED" } |
Example of ER Diagram
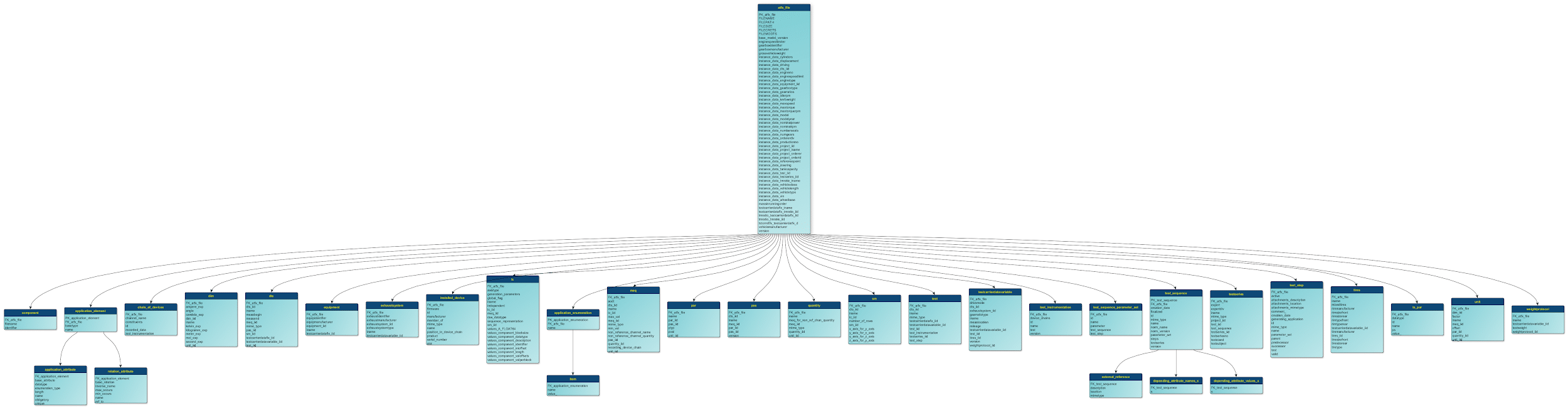
You can download the ER Diagram for the converted ASAM ODS XML file here.
Next we will run an SQL Query that selects “project_iname” element and its attributes.
|
1 2 3 4 5 6 7 8 9 10 |
SELECT af.instance_data_project_iname , ae."name" , ae.basetype , aa.base_attribute , aa."datatype" FROM atfx_file af JOIN application_element ae ON ae."FK_atfx_file" = af."PK_atfx_file" JOIN application_attribute aa ON aa."FK_application_element"= ae."PK_application_element" |
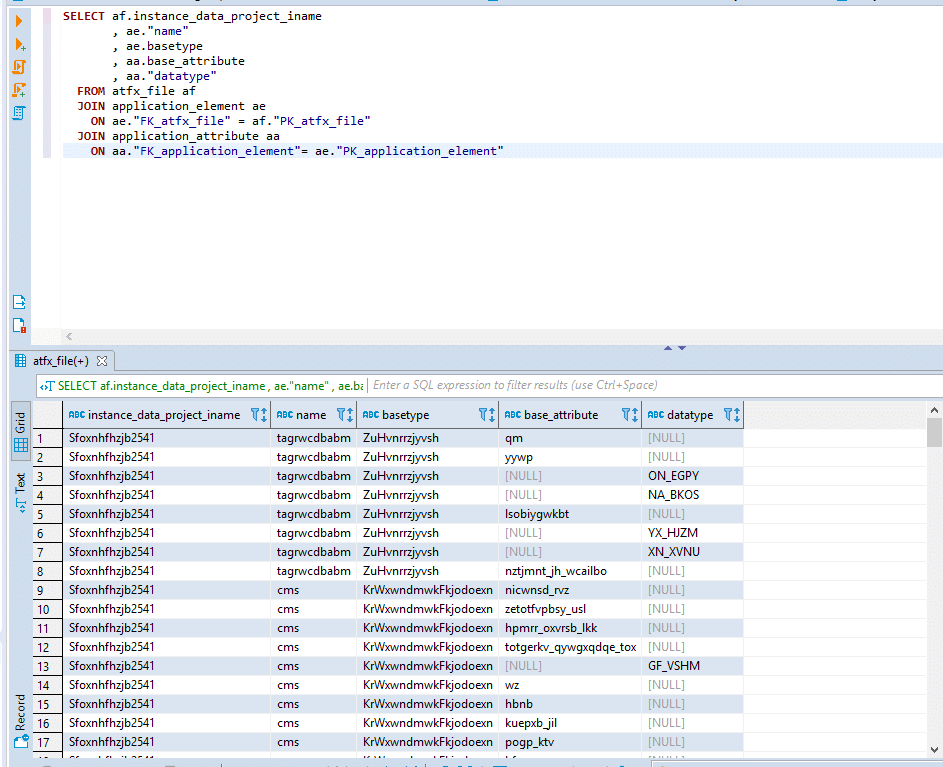
In the figure above you see the results of the query with obfuscated values.
Conclusion
We have shown you how easy it is to obfuscate and convert ASAM ODS XML with Paranoid and Flexter.
Our enterprise edition can be installed on a single node or for very large volumes of XML on a cluster of servers.
If you have any questions please refer to the Flexter FAQ section. You can also request a demo of Flexter or reach out to us directly.




